Are you a small business owner or a freelancer who offers services online? If so, you might be wondering how to get paid by your customers in a fast and convenient way. You might have tried different payment platforms. But they often require you to switch between different apps or websites. This can be time-consuming and confusing.
There is now another option to streamline the payment process. Microsoft has launched the Teams Payments app. This is a new feature that allows you to request and receive payments from your customers. You do it within Microsoft Teams meetings.
The Teams Payments app is currently available in the United States and Canada. Subscribers to Teams Essentials and Microsoft 365 business get it at no charge.
How Does the Teams Payment App Work?
The Teams Payments app is simple to use. You can get the app from the Microsoft AppStore. You add it to your Teams account and connect it to your preferred payment service. You can choose from:
- Stripe
- PayPal
- GoDaddy
Once you have set up the app, you can start requesting payments from your customers in Teams meetings.
How Do You Send a Payment Request?
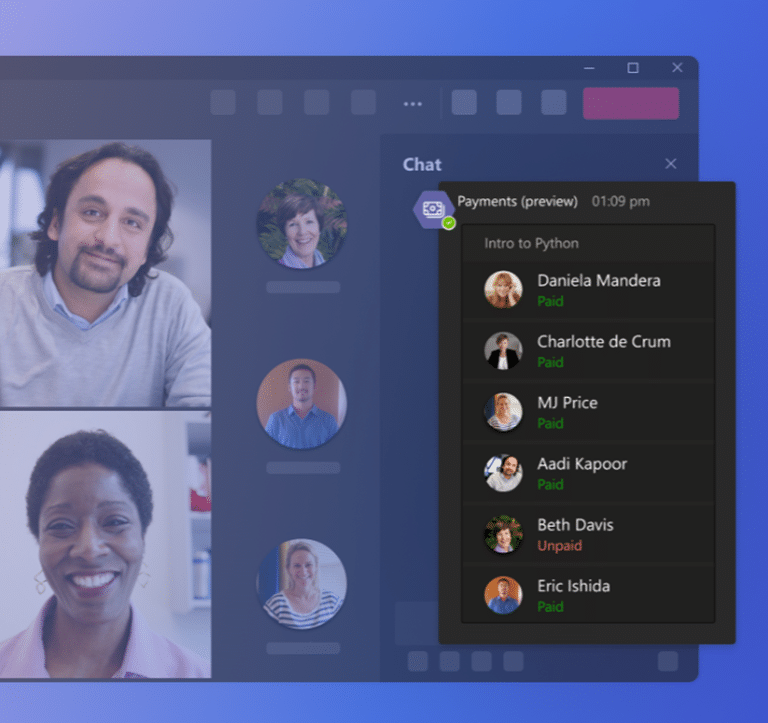
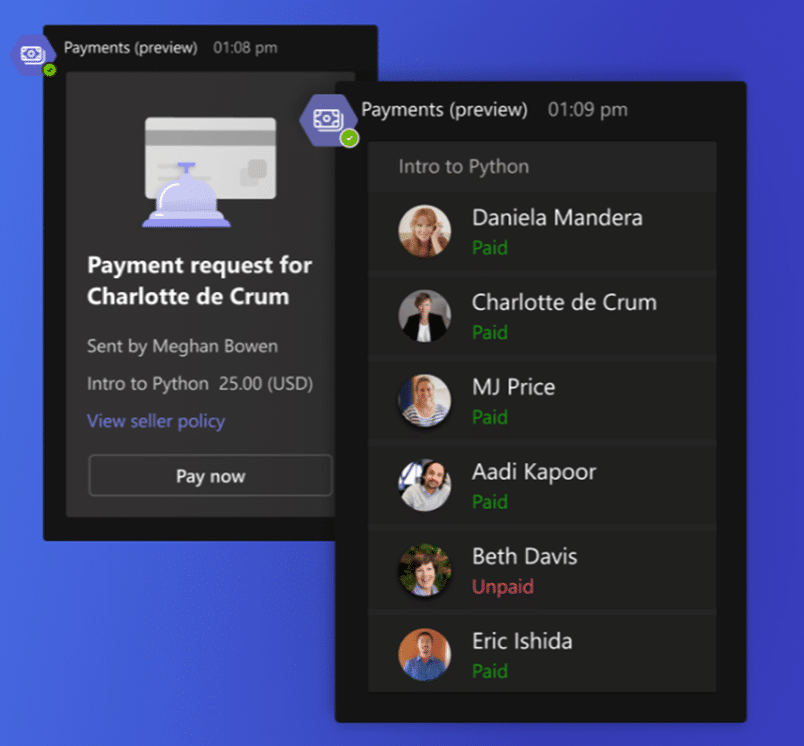
To send a payment request, you just need to open the meeting chat. Then, select the Payments icon from the messaging extensions. Then, you can fill out a simple form. It includes the amount, currency, description, and recipients of your request.
You can send the same request to several people if you want. The app will generate a card that shows the status of each payment, whether it is unpaid or paid.
Image credit: Microsoft
Your customers will see the same card in their meeting chat. They can click on the Pay Now button to complete their payment. The system will redirect them to the payment service that you have connected to the app. There, they can enter their payment details and confirm their transaction.
Once they have done that, they will see a confirmation message in the chat. You will receive a notification that your payment has been processed.
Image credit: Microsoft
Benefits of Using the Teams Payment App
The Teams Payments app has many benefits. Both for small businesses and freelancers who offer online services. Here are some of them:
It saves time and hassle.
You don’t need to switch between different apps or websites. You can easily request and receive payments from your customers. You can do everything within Teams meetings. This makes it more convenient and efficient for both parties.
It increases customer satisfaction and loyalty.
Your customers will appreciate the ease of paying you through Teams meetings. They don’t need to create an account or download an app to pay you. They can complete their transaction in a few clicks right inside the meeting.
It boosts your revenue and cash flow.
You can get paid faster and more securely by using the Teams Payments app. You don’t need to wait for invoices or checks to clear. You can receive your money within minutes of completing a service. Either directly into your bank account or PayPal account.
It enhances your professional image and credibility.
You can show your customers that you are using a reliable and trusted payment platform. One built by a well-known company that has been a technology leader for decades. You can also add a seller policy to your payment requests. Here you can specify your terms and conditions, cancellation policy, refund policy, etc.
It helps you keep track of payments.
Keeping track of payments is crucial for financial management. With the Teams Payments App, you can track transactions in real-time. You’ll receive instant notifications for successful payments. It will help you maintain a comprehensive record of your financial interactions.
It’s seamlessly integrated with Microsoft 365.
The Teams Payments App seamlessly integrates with Microsoft 365. You can leverage the power of Microsoft’s ecosystem. Using it to manage your communications, collaborations, and payments together. No need for more logins or complicated setups – it’s all within one platform.
It increases productivity.
Efficiency is the key to productivity. You reduce the time spent on payment-related tasks by integrating Payments into Teams. This efficiency translates into increased productivity. It allows you and your team to focus on core business activities and driving growth.
The Teams Payments app marks a significant leap in digital business transactions. By leveraging this powerful tool, you’re simplifying payments. You’re also enhancing customer experiences, ensuring data security, and boosting productivity.
We Can Help You Get More Out of Microsoft 365
The Teams Payments app is a great way to simplify and streamline your payment process. It can help you save time, increase customer satisfaction, and boost revenue.
Need help with this or other Microsoft 365 tools? Our experts can work with you to help you make the most out of your Microsoft subscription.
Give us a call today to schedule a chat.
Article used with permission from The Technology Press.










Recent Comments